Dynamic Analysis Using Drozer
Why
Drozer is a framework for Android security assessments developed by MWR Labs. Drozer allows you to assume the role of an Android app, and to interact with other apps, through Android’s Inter-Process Communication (IPC) mechanism, and the underlying operating system.
It helps to reduce the time taken for Android security assessments by automating the tedious and time-consuming tasks. It allows us to interact with the Dalvik VM, other apps’ IPC endpoints and the underlying OS.
What
We could use Drozer to do the following tests:
Discover and interact with the attack surface exposed by Android apps. Execute dynamic Java-code on a device, to avoid the need to compile and install small test scripts.
How
- Login to Androl4b Virtual Machine using the following credentials:
andro/andro - Click on the "Emulator" desktop icon.
Start the
drozer Agentapp and ensure thatEmbedded Serveris switched on.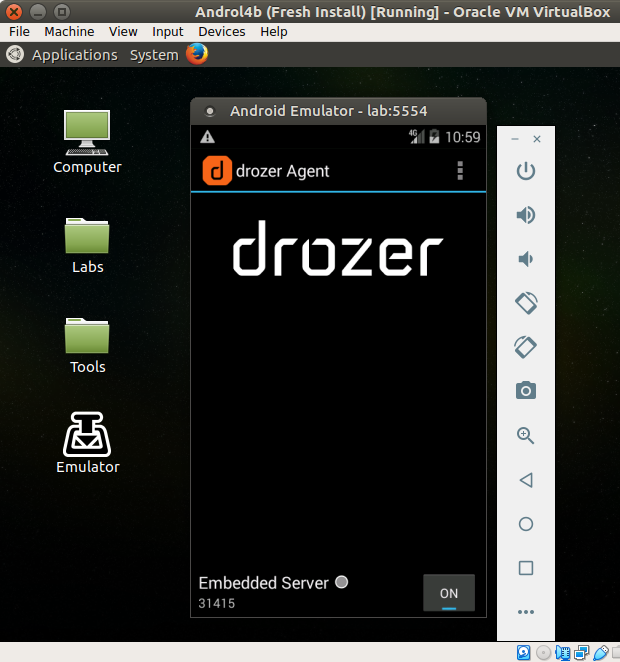
Click on
Terminusicon from the bottom tray, and select theNew terminaloption.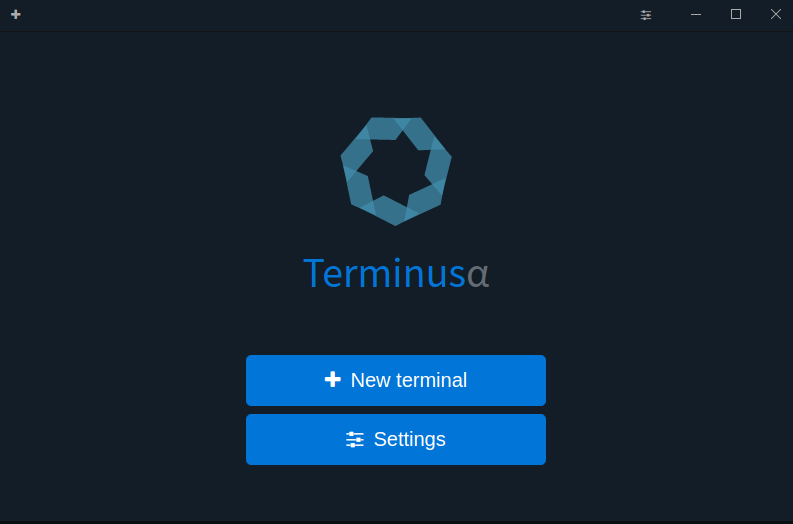
We need to set up a suitable port forward so that our PC can connect to a TCP socket opened by the drozer Agent inside the emulator, or on the device. By default, drozer uses port 31415. Run the following command in the terminal:
$ adb forward tcp:31415 tcp:31415Connect to drozer by running following command:
$ drozer console connectFor real mobile devices, we can specify the mobile device's IP address as shown below:
$ drozer console connect --server 192.168.0.10Use drozer to find security vulnerabilities. Follow the guidelines as specified in following link: http://mobiletools.mwrinfosecurity.com/Using-Drozer-for-application-security-assessments/.